Solution 2: The Edge web browser does not support S/MIME. See my recommendation above to see how to use Internet Explorer to read and send your encrypted emails when using OWA / webmail. Information ( from Microsoft ): To understand the problem with OWA, Edge, and S/MIME you need to know the OWA S/MIME is an Active-X control. Secure Email Reader will delete the file from your mobile device after successfully importing the key material. Next time you see an smime.p7m or smime.p7s attachment in Mail or in your web mail client, just open it using Secure Email Reader. You’ll be able to decrypt it and access any attachments. Secure Email Reader for Android.

We like to use encrypted email when we have sensitive conversations. One consistent annoyance we’ve found when we encrypt our messages, though, is that it reduces the usefulness of our mobile devices. We can see that we’ve received an encrypted message, but can’t read the message until we return to a desktop machine with access to the appropriate keypair.
Our mobile SMIME reader apps enable us to read these messages securely on our devices. Our iPhone/iPad app is now available in the App store. A version for Android phones is now available in the Android Market.
Protecting your private keys
In order to read encrypted email on your phone, you naturally need to install your keypair on the device. While it’s conceptually very simple to do so, keeping your keys secure requires some care. First, you need to export your keypair from your desktop mail client into a PKCS#12 file. You’ll want to choose a very strong passphrase for this file, because anyone who has the file and can get your passphrase will be able to read your encrypted messages. Unfortunately, entering a very strong passphrase into the tiny keyboards that accompany mobile devices is (unsurprisingly) quite difficult. To assist with this, we’ve built a small utility for Mac and Windows that allows you to generate a QR code containing your passphrase, and enabled our mobile apps to read passphrases from this barcode. Our Barcode Generator utility even includes a random passphrase generator to help you choose a strong one. Since you’ll never need to type this passphrase manually, you can make it as complex as you like.
Getting Started
You need your private key on your device in order to read encrypted email. Installing these keys is a little bit different depending on the device you’re using.
| [Jump to iPhone/iPad] | [Jump to Android-based devices] |
Exporting your keys from the desktop
First, you’ll need to export your keypair to a PKCS#12 file. We recommend starting by launching Barcode Creator and generating a good strong passphrase. Barcode Generator will place the passphrase on the clipboard, display a QR code and allow you to print or save the QR code. Next, export your keys using the utility supplied with your mail reader, pasting the newly generated strong passphrase from the clipboard when prompted to enter a passphrase.
On Mac OS X, just launch Keychain Access, select your certificate and choose “Export.”
On Windows, find your certificates in Internet Options, select the one you want to export and click “Export…”.
On either platform, be certain to use either “PKCS#12” or “PFX” format.
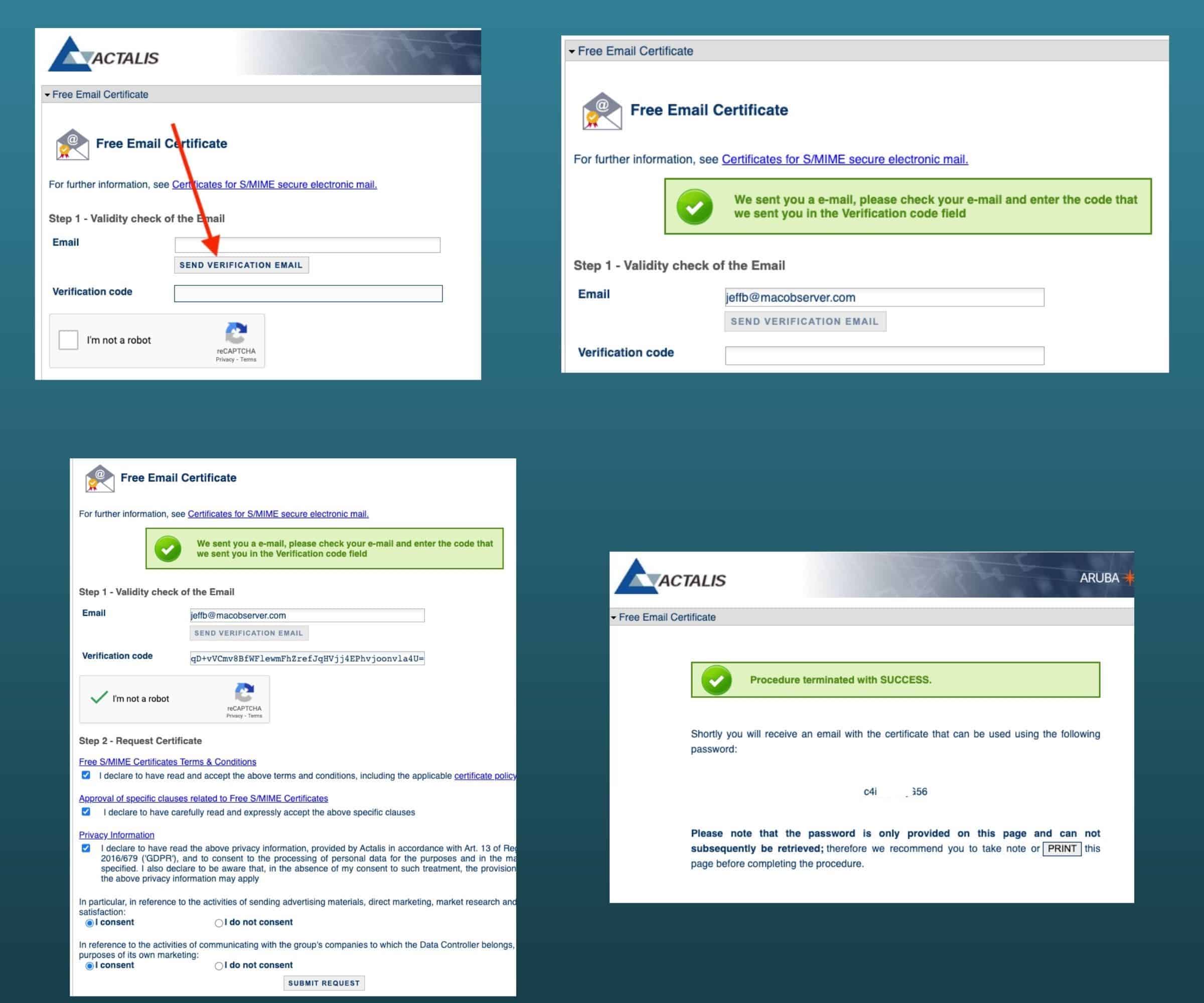
Secure Email Reader for iOS
Once you have your key saved in a PKCS#12 file, use iTunes to share the file with the Secure Email Reader.
Then start the secure email reader and import the keys, scanning the barcode you saved when it requests a passphrase. If the import does not start when you launch Secure Email Reader, click the green plus sign icon in the bottom right hand corner of the main screen to start the import. Secure Email Reader will delete the file from your mobile device after successfully importing the key material.
That’s it! Next time you see an smime.p7m or smime.p7s attachment in Mail or in your web mail client, just open it using Secure Email Reader. You’ll be able to decrypt it and access any attachments.
Secure Email Reader for Android
Once you have your key saved in a PKCS#12 file, copy your key to the device’s storage, either using a USB cable, a bluetooth file transfer, or by connecting the SD card to your computer.
Then start the secure email reader and choose the keystore option from the menu. Tap import, and scan the bar code you saved when it requests a passphrase. You’ll then need to choose a passphrase you’ll enter every time you want to decrypt a message. We recommend using a bar code for this as well, and keeping it some place secure, like a wallet.
Step 1: Enter the passphrase you used to protect the .p12 file
Step 2: Enter the passphrase you’ll use when you decrypt email.
Step 2: Enter the passphrase you’ll use when you decrypt email.
That’s it! Next time you see an smime.p7m or smime.p7s attachment in Mail or in your web mail client, just open it using Secure Email Reader. You’ll be able to decrypt it and access any attachments.
-->S/MIME (Secure/Multipurpose internet Mail Extensions) is a widely accepted protocol for sending digitally signed and encrypted messages. S/MIME in Exchange Online provides the following services for email messages:
- Encryption: Protects the content of email messages.
- Digital signatures: Verifies the identity of the sender of an email message.
S 2fmime Reader Free
The rest of this article generally describes S/MIME and how these services work.
To configure S/MIME in Exchange Online, see the following topics:
S/MIME digital signatures
Digital signatures are the more commonly used service of S/MIME. As the name suggests, digital signatures are the digital counterpart to the traditional, legal signature on a paper document. As with a legal signature, digital signatures provide the following security capabilities:
Authentication: A signature serves to validate an identity. It verifies the answer to 'who are you' by providing a means of differentiating that entity from all others and proving its uniqueness. Because there is no authentication in SMTP email, there is no way to know who sent a message. Authentication in a digital signature solves this problem by allowing a recipient to know that a message was sent by the person or organization who claims to have sent the message.
Nonrepudiation: The uniqueness of a signature prevents the owner of the signature from disowning the signature. This capability is called nonrepudiation. Thus, the authentication that a signature provides gives the means to enforce nonrepudiation. The concept of nonrepudiation is most familiar in the context of paper contracts: a signed contract is a legally binding document, and it is impossible to disown an authenticated signature. Digital signatures provide the same function and, increasingly in some areas, are recognized as legally binding, similar to a signature on paper. Because SMTP email does not provide a means of authentication, it cannot provide nonrepudiation. It is easy for a sender to disavow ownership of an SMTP email message.
Data integrity: An additional security service that digital signatures provide is data integrity. Data integrity is a result of the specific operations that make digital signatures possible. With data integrity services, when the recipient of a digitally signed email message validates the digital signature, the recipient is assured that the email message that is received is, in fact, the same message that was signed and sent, and has not been altered while in transit. Any alteration of the message while in transit after it has been signed invalidates the signature. In this way, digital signatures provide an assurance that signatures on paper cannot, because it is possible for a paper document to be altered after it has been signed.
Important
Although digital signatures provide data integrity, they don't provide confidentiality. Messages with only a digital signature are sent in clear text, like SMTP messages and can be read by others. In the case where the message is opaque-signed, a level of obfuscation is achieved because the message is base64-encoded, but it is still clear text. To protect the contents of email messages, encryption must be used.
S/MIME encryption
Message encryption provides a solution to information disclosure. SMTP-based internet email does not secure messages. An SMTP internet email message can be read by anyone who sees it as it travels or views it where it is stored. These problems are addressed by S/MIME using encryption. Encryption is a way to change information so that it cannot be read or understood until it is changed back into a readable and understandable form. Message encryption provides two specific security services:
Confidentiality: Message encryption serves to protect the contents of an email message. Only the intended recipient can view the contents, and the contents remain confidential and cannot be known by anyone else who might receive or view the message. Encryption provides confidentiality while the message is in transit and in storage.
Dataintegrity: As with digital signatures, message encryption provides data integrity services as a result of the specific operations that make encryption possible.
Important
S/mime Reader Windows 7
Although message encryption provides confidentiality, it doesn't authenticate the message sender in any way. An unsigned, encrypted message is as susceptible to sender impersonation as a message that isn't encrypted. Because nonrepudiation is a direct result of authentication, message encryption also doesn't provide nonrepudiation. Although encryption does provide data integrity, an encrypted message can show only that the message hasn't been altered since it was sent. No information about who sent the message is provided. To prove the identity of the sender, the message must use a digital signature.
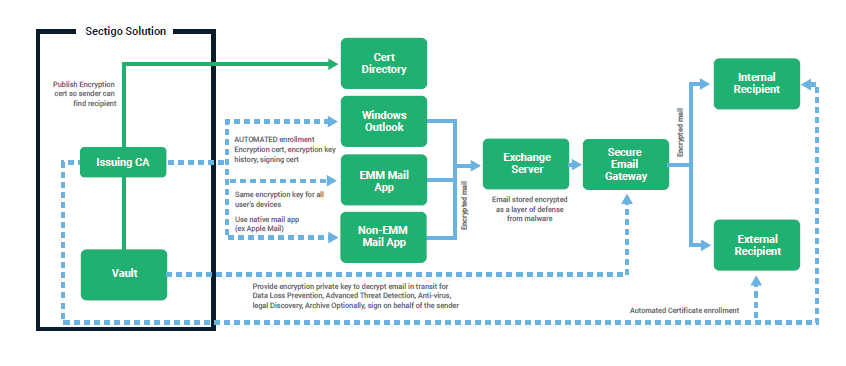
Related message encryption technologies
Other encryption technologies work together to provide protection for messages at rest and in-transit. S/MIME can work simultaneously with the technologies in the following list, but is not dependent on them:
- Transport Layer Security (TLS) which replaces Secure Sockets Layer (SSL):
- Encrypts the tunnel or the route between email servers in order to help prevent snooping and eavesdropping.
- Encrypts the connection between email clients and email servers.
- BitLocker: Encrypts data on hard drives in client computers and servers. If an unauthorized party somehow gains access, they can't read the data on the drives.
S/mime Reader Windows
Office 365 Message Encryption is a direct competitor to S/MIME, and has the following advantages over S/MIME:
S/mime Reader Mac
- It's a policy-based encryption service that's configured by an admin to encrypt messages that are sent to anyone inside or outside of the organization. In contrast, users are required to decide whether to apply or not apply S/MIME to messages that they send.
- It's an online service that's built on Azure Rights Management (Azure RMS) and does not rely on a public key infrastructure. In contrast, S/MIME requires a certificate and certificate publishing infrastructure.
- Office 365 Message Encryption provides additional capabilities. For example, you can customize messages with your organization's brand.